Today, I run into an issue by adding a service principal to a workspace. To my experience so far, this should be straight forward and a matter of adding with the right permissions in the workspace settings. However, for some reason I couldn’t get it to work. In this blog I will elaborate on what caused this issue and which tenant setting influences this.
Case
At a client, I wanted to add a service principal to a workspace to make sure we have service-to-service connectivity in a secure way, but not based on a service account or named user. The service principal was the way to go to make sure Azure Data Factory could authenticate to any workspace artifacts in Fabric / Power BI.
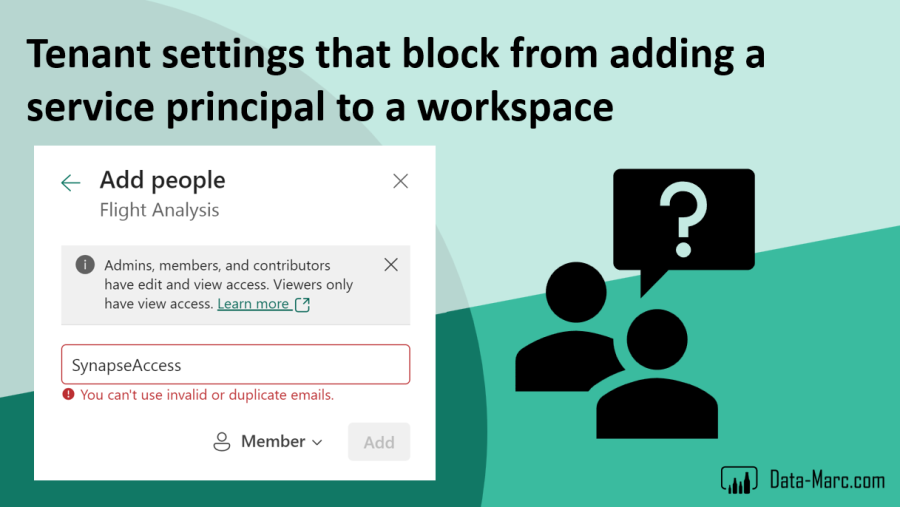
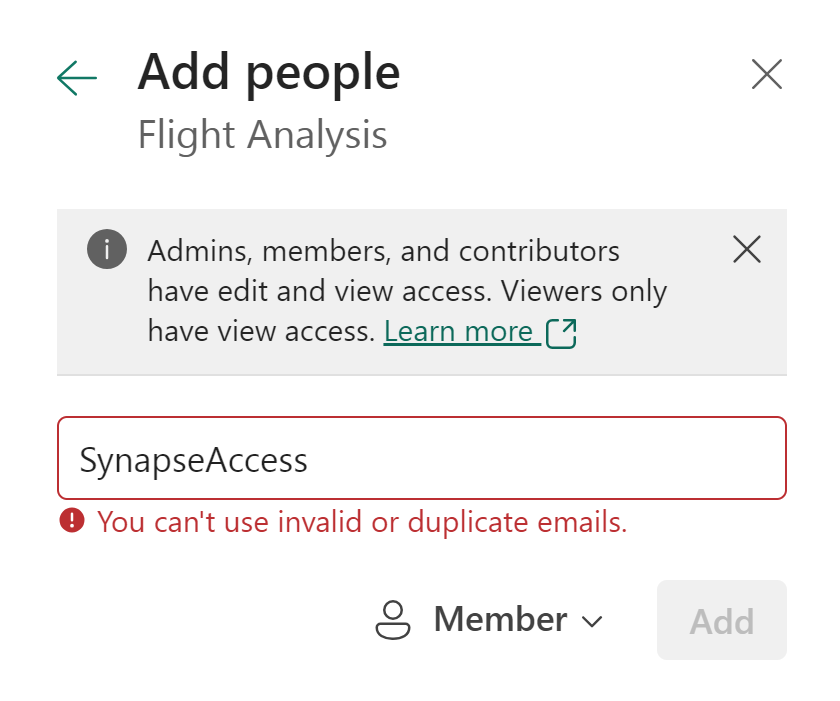
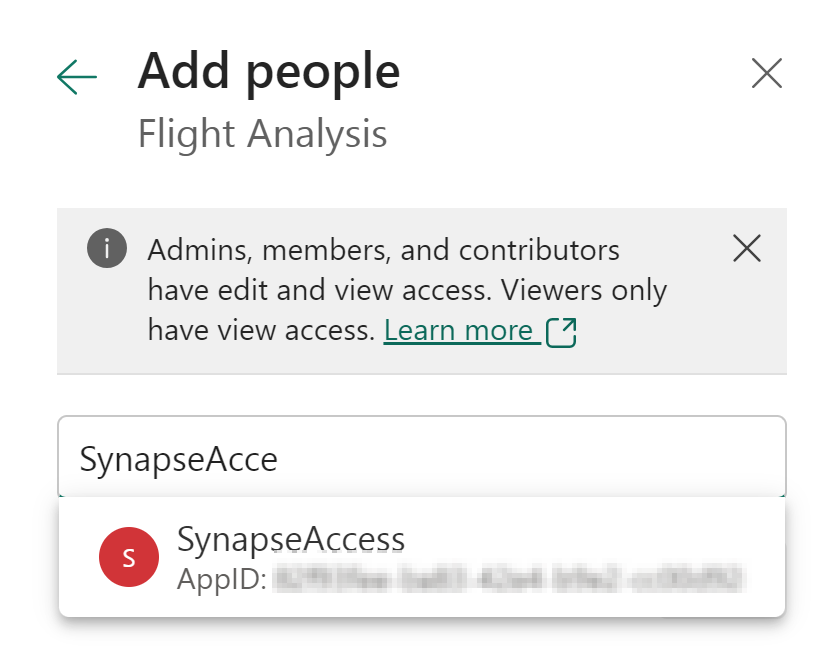
After creating the service principal in Entra ID (Azure Active Directory), it was a matter of just adding it in the workspace access menu, I thought. But I was wrong… When I entered the name of the service principal in dialog to add to the workspace, it showed the service principal had an invalid or duplicate email, which was totally confusing to me. See below screenshot as example.
After trying a few times, with different workspaces, it kept showing this issue. I tried to find the right documentation, but all I found was a page describing automation in Power BI through service principals. This documentation showed that the tenant setting “Allow service principals to use Power BI APIs” must be enabled.
Resolution
Stubborn as I am, I first judged the documentation and though it was wrong. Simply because it talks about Power BI APIs and that was not what I was trying to achieve here. I just wanted to have authentication between two services arranged.
Again, I went through all tenant settings to check if I overlooked one that talked specifically about service principal access but couldn’t find any. So, I decided to try out a few things on my own playground tenant, the tenant setting I judged before to start with.
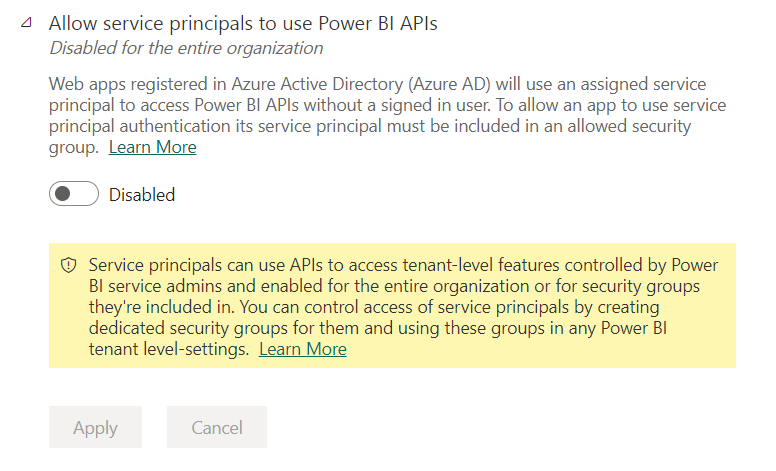
Reading the description of the tenant setting, I says:
Allow service principals to use Power BI APIs
Web apps registered in Azure Active Directory (Azure AD) will use an assigned service principal to access Power BI APIs without a signed in user. To allow an app to use service principal authentication its service principal must be included in an allowed security group. Learn more
Clicking the learn more link, was not helping me at all, since that references to a case of Power BI Embedded. Again, not what I was trying to achieve. However, I just flipped the switch to see what would happen.
Surprisingly enough, that works! After setting it to enabled, the service principal showed up in the list of suggestions when I typed the name in the workspace access dialog.
What did I learn? Maybe to be a bit less stubborn. But at the same time, the descriptions of the tenant settings, as well as the documentation pages are not always clear in what a specific tenant setting is exactly enabling or disabling. By sharing it here, I hope it helps other people to find out easier what could cause a similar challenge on their end.